2021网刃杯WP
2021网刃杯WP
成绩


第二名
MISC部分
气死我了气死我了气死我了
私钥头错了一直卡着,过了就好说多了。
注:encrypted ad1是赛后出的
签到
解压得到flag.txt和一段密文
Flag.txt是0宽
勾选BCDE(vim查看就可以看到要勾选这几个)、得到hint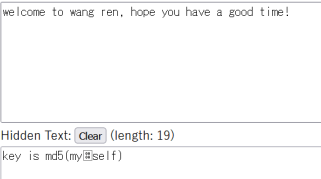
myself居然是flag.txt的md5,我麻了
得到key:f71b6b842d2f0760c3ef74911ffc7fdb
最后测试rabbit,得到flag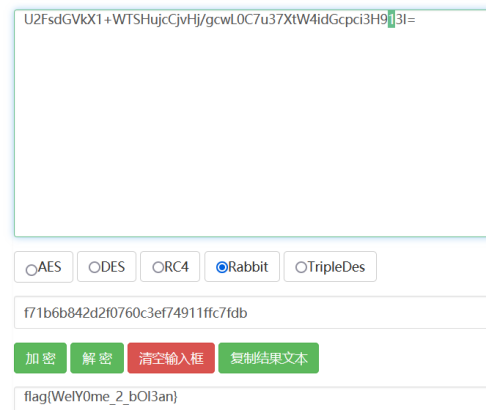
flag{WelY0me_2_bOl3an}
baby-usb
键盘流量,完全按这篇即可
http://www.ga1axy.top/index.php/archives/22/
脚本直接用,步骤直接仿
得到
output :
CT[DEL]ONH[DEL]GRATUE[DEL]LATIOKE[DEL][DEL]NSONFINY[DEL]DINGMEBUTIWII[DEL]LLNS[DEL]OTTELLYOUWHERETQA[DEL][DEL]HEPZ[DEL]ASSWORDWS[DEL][DEL]OX[DEL]FWE[DEL]OD[DEL]RDDOC[DEL]CUMENTISGOARFV[DEL][DEL][DEL]NDFINDITAGAIN
发现删除的就是KEY,
The key is qazwsxedcrfv
即可打开word
flag{685b42b0-da3d-47f4-a76c-0f3d07ea962a}
Mspaint
上vol,imageinfo显示Win7,pslist发现用了cmd、画图、ie,cmd说他喜欢把图片截图下来,因此filescan |grep ‘png’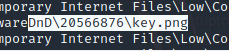
导出,发现文件只有一个hack
然后iehistory发现他访问了一个百度云盘链接,尝试用hack,成功。密码即hack。下载下来附件,居然有密码。
因此查看内存图,方法如此链接最后一个
https://blog.csdn.net/qq_42880719/article/details/117304586
因为我怕看错(主要是我眼比较瞎),所以我用zip爆破软件,用户自定义爆
我选择了8%R~sSA52!iqp,长度8位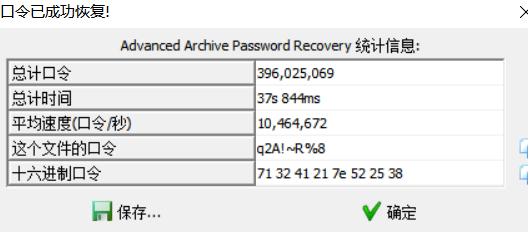
解压之后,发现是python写的
于是直接逆
参考:https://blog.csdn.net/weixin_44362969/article/details/105616531 |
得到
key = 'xxxxxxxxxxxxxxx' |
然后现在需要找key,但是我们知道flag{开头,因此可以反推出key前5位
f = [18,4,80,20,36] |
得到th1s_,直接winhex搜key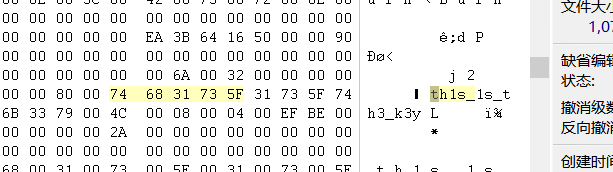
keys = 'th1s_1s_th3_k3y' |
其实这里预期搜key应该是内存取证用screenshot指令,可以看到key
flag{20708c15-eb55-4cbc-930b-68de15c55b32}
encrypted ad1
积累了,学到了。是我傻了
下载下来文件名为ZW5jcnlwdA,解码之后得到encrypt
结合题目为ad1,所以应该是一个ad1的磁盘文件,并且加了密
查看文件尾,能够看到一串base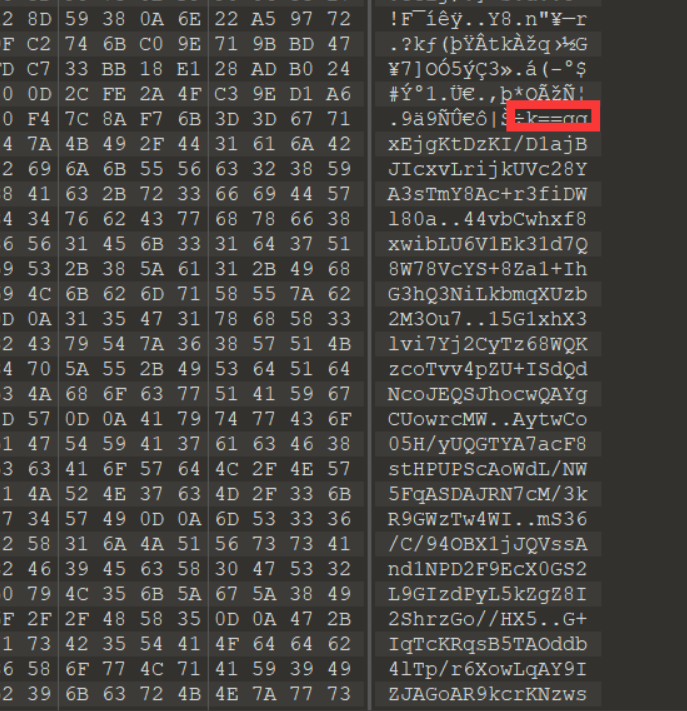
但很明显,这里转过来了,因此复制出来脚本转一下
s = '''==gqxEjgKtDzKI/D1ajBJIcxvLrijkUVc28YA3sTmY8Ac+r3fiDWl80a |
得到一个base串,看了之后应该类似于RSA之类的。
然后打开搞磁盘文件常用的FTK,发现FTK能解密,于是为了研究,主动去生成了一个ad1
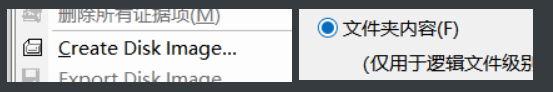
然后反正就生成一个ad1,记得生成的文件给他加个密
注意到正确的文件头应该是41 44
于是将题目的文件尾base删掉、文件头00 00 改成 41 44
然后FTK里点击decrypt ad1选项
可以注意到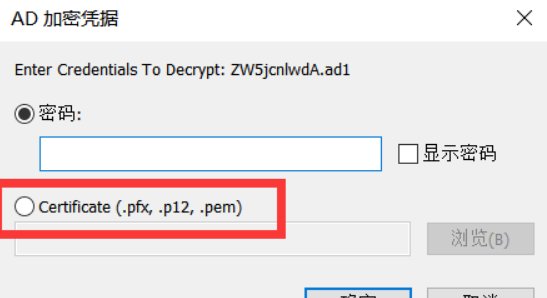
能使用证书来解密,于是尝试。
然鹅比赛期间我一直没添加—–BEGIN RSA PRIVATE KEY—–头和—–END RSA PRIVATE KEY—–尾,一直是加的—–BEGIN PRIVATE KEY—–,导致没解出来,我麻了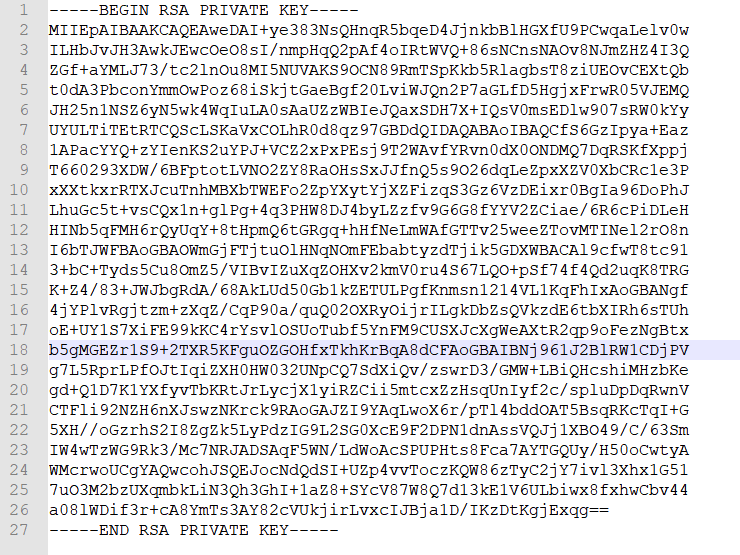
如图,然后保存为pfx文件。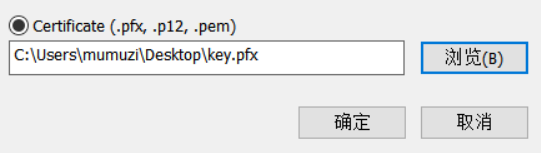
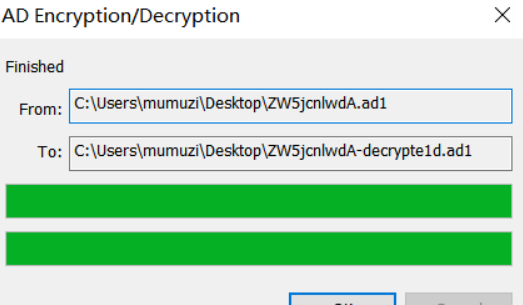
解密之后,用FTK挂载此文件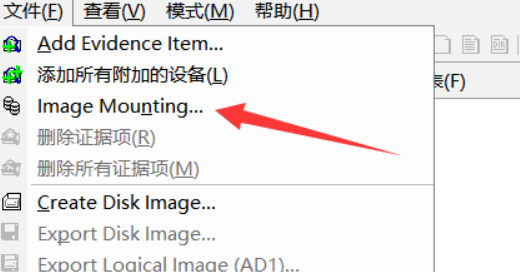
这里我挂载到了H盘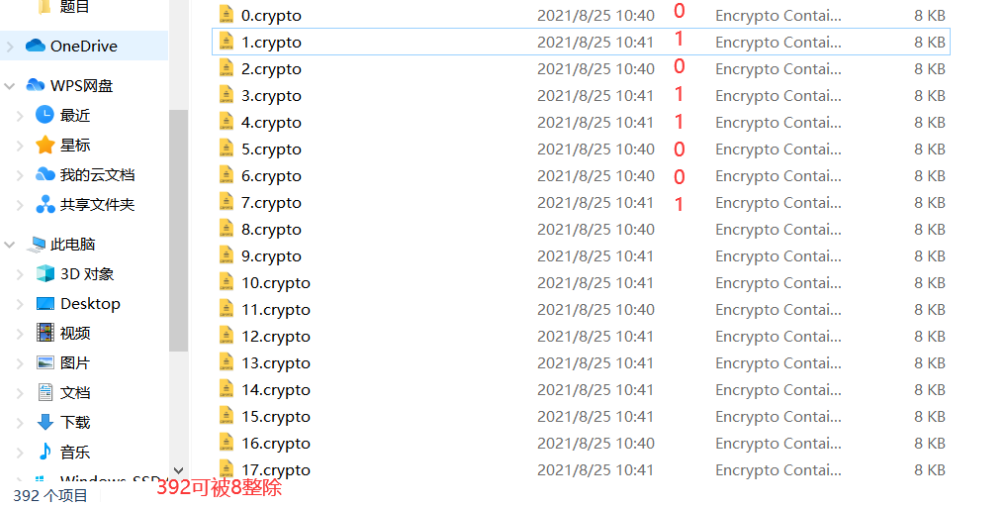
直接想到时间来作为2进制,2进制转ascii
于是写个脚本转换
import os |
得到
You are so cool!!! this is your key: 6a90383cd08c
然后这392个文件是crypto文件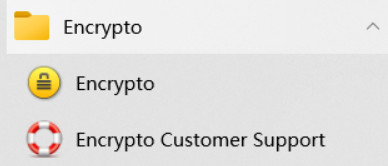
用这个,然后用这个key来解0.crypto和1.crypto(因为这两个时间不一样)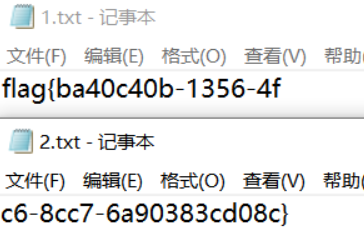
flag{ba40c40b-1356-4fc6-8cc7-6a90383cd08c}
协议
藏在s7里的秘密
下载下来的流量包是部分损坏的,使用网站在线修复
http://f00l.de/hacking/pcapfix.php
然后打开流量包,发现有png,但是就如此提取,必定会混入奇奇怪怪的东西
于是观察之后,用tshark来提取
tshark -r Ks3qlAF1bTuysqpJ.pcap -T fields -e s7comm.resp.data -Y “s7comm.param.func == 0x05 and ip.src==192.168.139.1” > png.txt
得到16进制数
用010打开,将十六进制数复制进去,即可得到图片,但是明显发现高度不对,因此修改任意高度,得到flag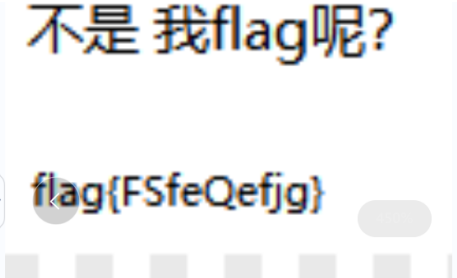
flag{FSfeQefjg}
老练的黑客
和之前工控的那道,不能说是完全相似,只能说是一模一样
类原题博客&&赶快关注工控大佬的博客
根据此博客,能直接找到错误的值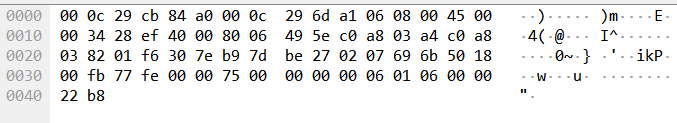
第1199流找到22b8
然后根据观察前面的流,发现read的值是跟在过滤之后的第2个流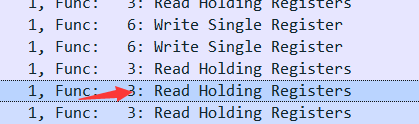
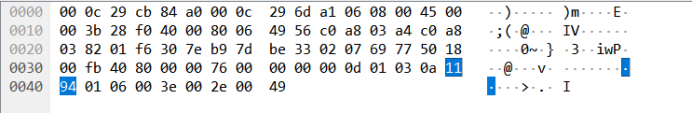
然后尝试理解提交
flag{22b81194}
Reverse
reverse1
SM3
然后把下图的复制进脚本
百度一个国密SM3脚本
from math import ceil |
倒数第5的flag = ‘’+k,每次输出一个,将将其填入,直到最后即可
当最后填入wel30m_t0_sm3!!!
此时输出空白,则此为key
flag{g0042ye_t0_sm4}
2048小游戏
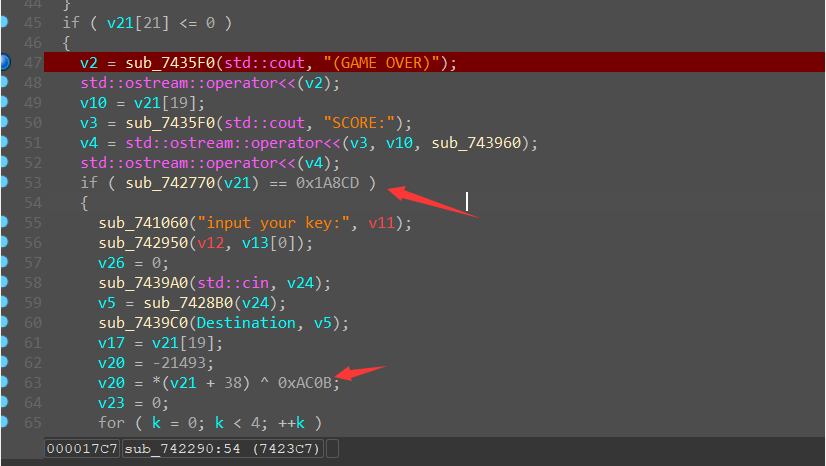
一个不知道啥鬼游戏,找到有flag的逻辑
有个不知道什么的运算。但是经过几次测试,发现分数越多,那个函数得到的值越小。,那就i慢慢凑出来,发现分数为0x2100时刚好满足条件,然后下面就是根据这个分数,异或一个固定值得到一个数,然后下面就是验证前四个数值,就是上面那个数的倒数,然后下面就是对0x2100%8+48,0x2100/8
|
最后
flag{b0d800402}
web
ez_sql
和Inctf的Rssa其中的一个小点考点相同,直接改脚本即可
原文连接:https://www.yuque.com/docs/share/f2e36905-38ae-4c20-8749-5aba747e5b91?#
#-- coding:UTF-8 -- |
flag为53a2d36d72760586dfc400e54b54564b
ez_web
考点:文件读取、Python反序列化
右键注释中获得<!-- ?pic=1.jpg -->,发现是一个任意文件读取,使用http://116.62.239.41:4322/?pic=/app/app.py读取源文件,源码如下
import pickle |
知道了是python的反序列化漏洞,这里直接用巅峰极客2021 opcode的Payload即可
import base64 |
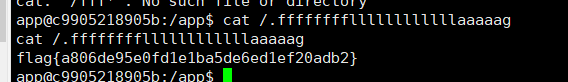
获得flagflag{a806de95e0fd1e1ba5de6ed1ef20adb2}
ez_php
构造POP链如下
|
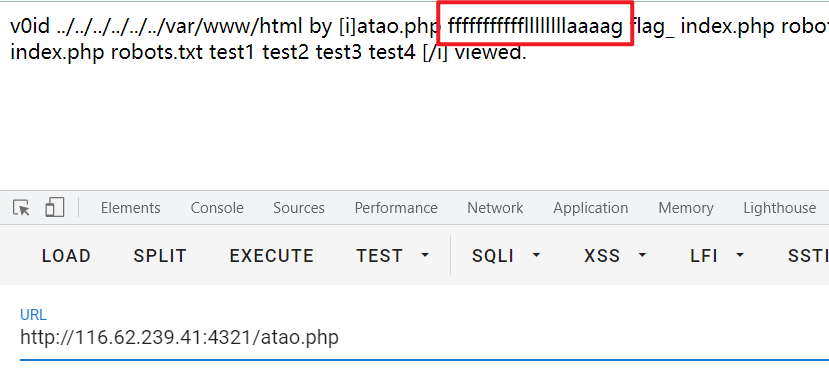
接着访问fffffffffffllllllllaaaag文件,下载下来
直接获得flagflag{v3rY_Ez_Php_P0p}
2021网刃杯WP
1.2022第二届网刃杯WP
2.2021NCTF比赛WP
3.2021安询杯wp
4.2021陇原战疫WP
5.2021bytectf线上WP
6.2021绿城杯wp
7.2021第一届长城杯网络安全大赛WP
8.2021第五空间大赛WP