2021安询杯wp
2021安询杯wp
Misc
应该算是签到
来得早不如来的巧
CyzCC_loves_LOL
小脑洞+老考点,理解一下
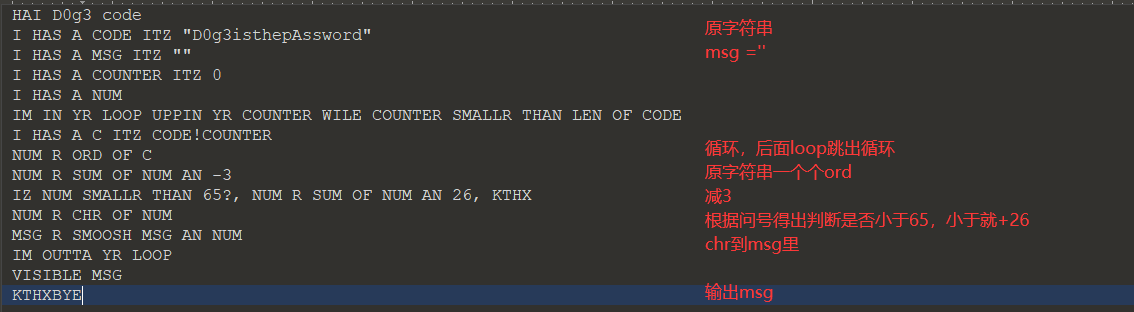
其实是放进百度翻译然后一下看出来了
s = 'D0g3isthepAssword' |
密码为AGdJfpqebmXpptloa
然后解压得到图片和图片(
jpg那个图说是silent,于是知道是silenteye,右边的图不是piet就是brainloller,试了之后发现是brainloller
然后.\bftools.exe decode brainloller .\Program.png,得到的brainfuck解码一下得到0MTTW CWZVN!,空格替换下划线即可
然后silenteye解jpg,密码为0MTTW_CWZVN!
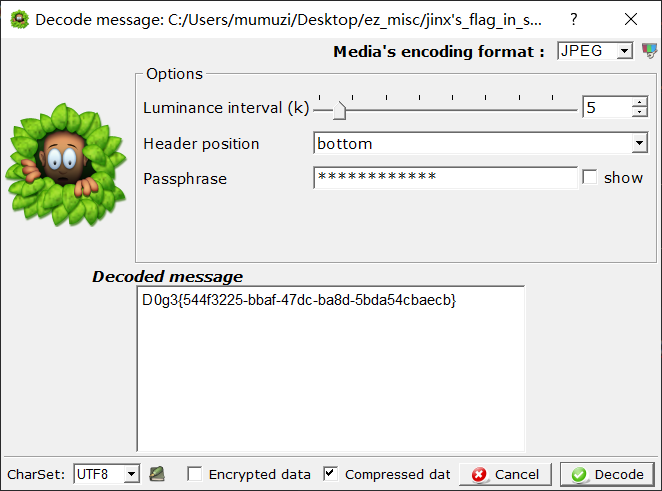
D0g3{544f3225-bbaf-47dc-ba8d-5bda54cbaecb} |
Cthulhu Mythos
hint.mp3是sstv,后面那段扫一下即可

解码

根据提示猜测是泰拉瑞亚,去github下载一个地图编辑器

进去就看到7I4YF6QL0
然后猜测剩下的在对话里之类的,之后在分析里找到内容
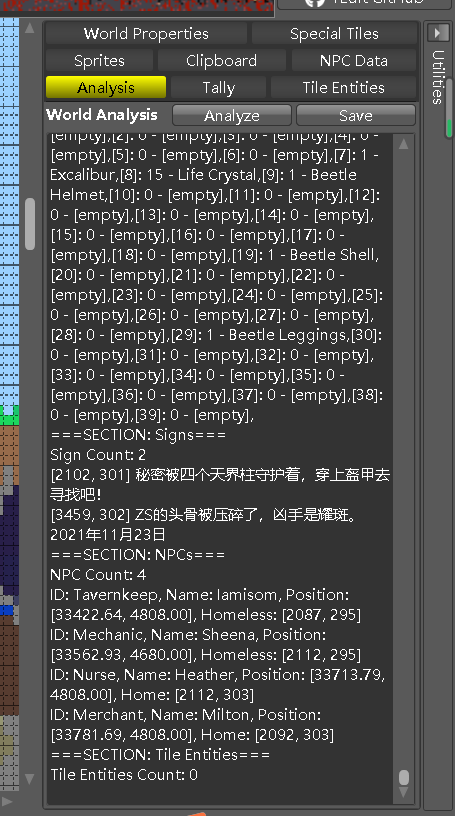
导出后看txt
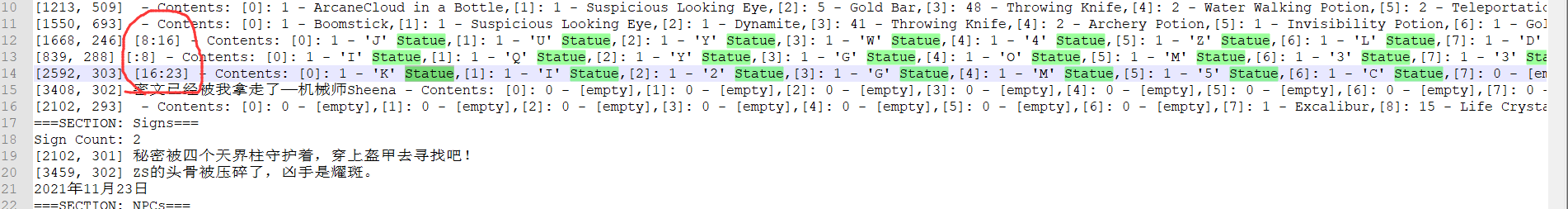
按顺序撸下来,得到
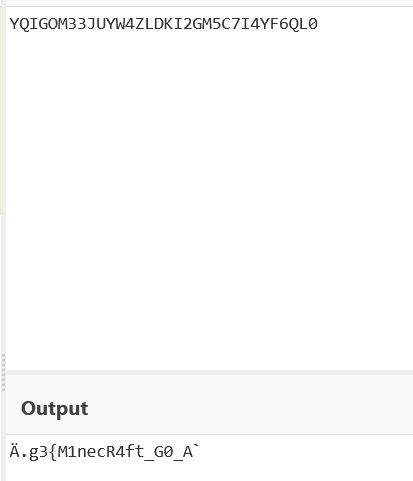
emm能看出来前面和后面都有错误,但是前面能知道是D0g3{M1necR4ft_G0_A 后面是d_Try_Terr4ria!}
然后觉得中间填and,尝试提交发现正确,所以flag为
D0g3{M1necR4ft_G0_And_Try_Terr4ria!} |
lovemath
爆CRC
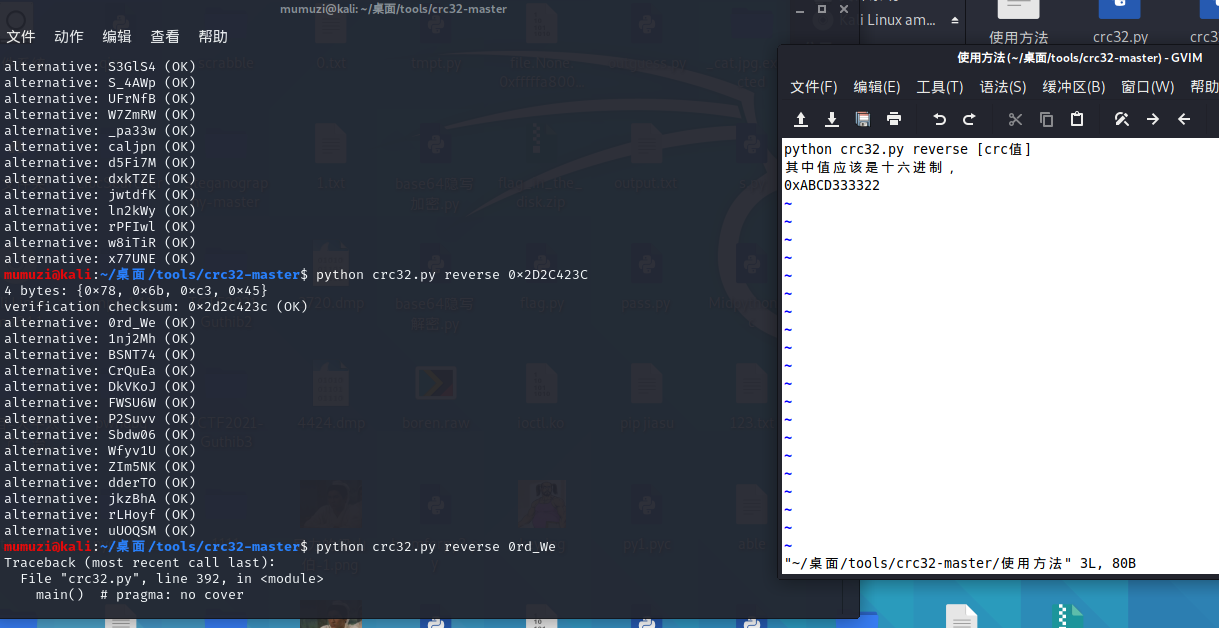
得到密码
th1s_Is_Y0ur_pa33w0rd_We1c0m3e
blind是LSB,BGR的,提取出来一个图片纯数字
然后用QQ OCR一下
1251077695482776025338577125579215707216262981842821000162276994967943212822693842845266851984880336702446444408289977864567921038435144120176357529686342977212633764247620567669441602729004003473312468776582473461071462631554533766709934484393185739708817165738912742570170547790145328253304755428563911689057632001795598667127514331122190795355921436735375126688142856470280128821316586008242687241930886868804388482643589009068543771977163419519208340324352 |
结合题目给的甚至能画出自己
找到了塔珀自指公式,然后github发现有解码的网站
http://keelyhill.github.io/tuppers-formula/
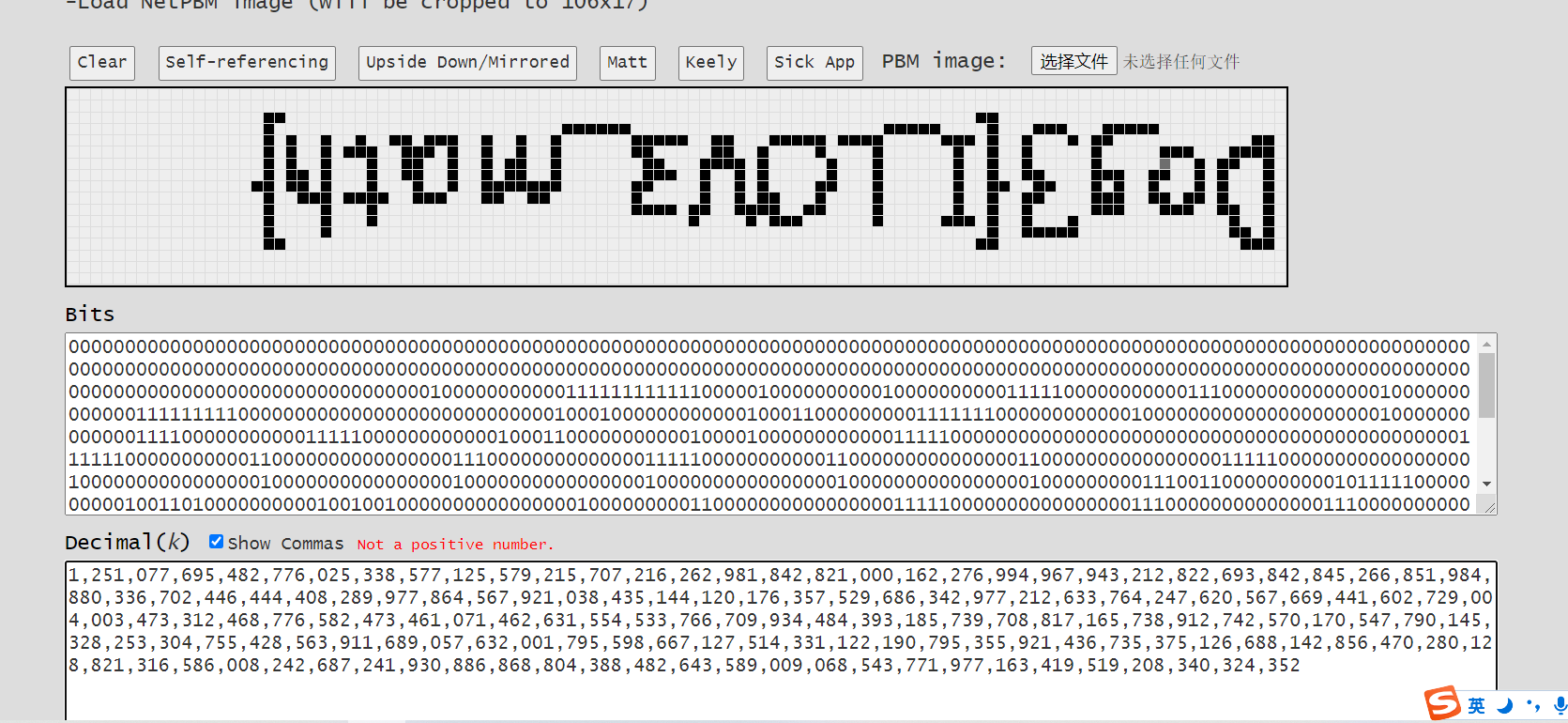
反过来看即可
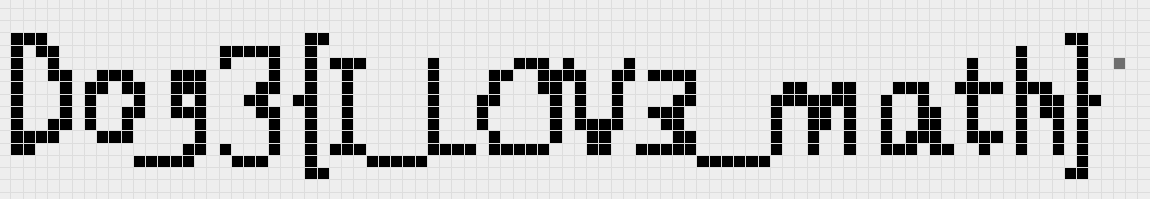
D0g3{I_LOV3_math} |
Pwn
stack
格式化字符串泄露基地址和canary,计算出pop,system,/bin/sh在程序中的地址然后栈溢出即可
from pwn import * |
连上之后cat sky_token然后exit输入sky_token即可
本来一开始是windows跑的每次exit输入sky_token都显示我错误,只好去打开ubuntu老老实实跑一下了
noleak
1.思路:off by null打__free_hook
from pwn import * |
Re
sign_in
一个贪吃蛇游戏(又是一个嵌屎的题)
smc

直接动调,然后手动改跳转进入该函数。
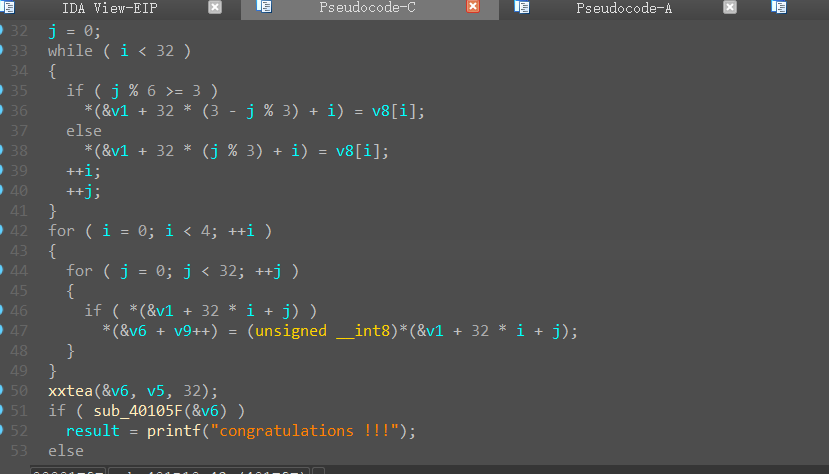
是shuffle+xxtea
先解xxtea
因为我是改条件跳转的,所以要爆破delta。
|
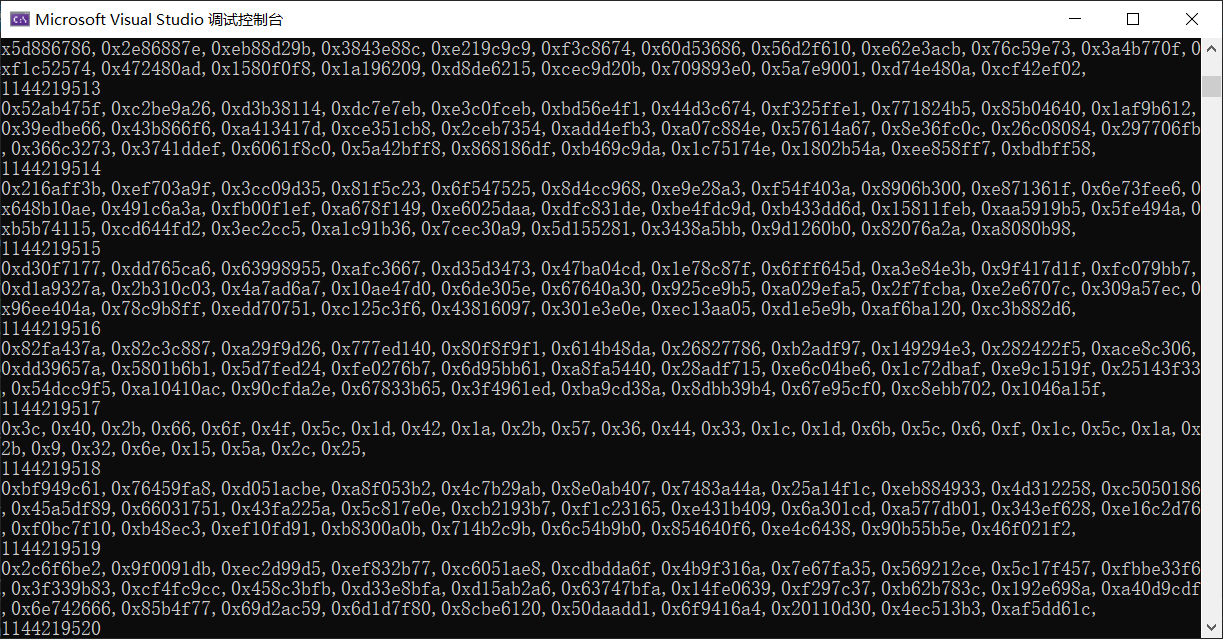
得到:
0x3c,0x40,0x2b,0x66,0x6f,0x4f,0x5c,0x1d,0x42,0x1a,0x2b,0x57,0x36,0x44,0x33,0x1c,0x1d,0x6b,0x5c,0x6,0xf,0x1c,0x5c,0x1a,0x2b,0x9,0x32,0x6e,0x15,0x5a,0x2c,0x25 |
然后shuffle可以先算出他的偏移值,然后直接还原就可
m=[0x3c,0x40,0x2b,0x66,0x6f,0x4f,0x5c,0x1d,0x42,0x1a,0x2b,0x57,0x36,0x44,0x33,0x1c,0x1d,0x6b,0x5c,0x6,0xf,0x1c,0x5c,0x1a,0x2b,0x9,0x32,0x6e,0x15,0x5a,0x2c,0x25] |
virtus
他释放了一个文件?(这是一个拉屎的题)但是我找不到,不知道是不是权限问题,然后我用Resource Hacker直接梭哈出一个资源文件,
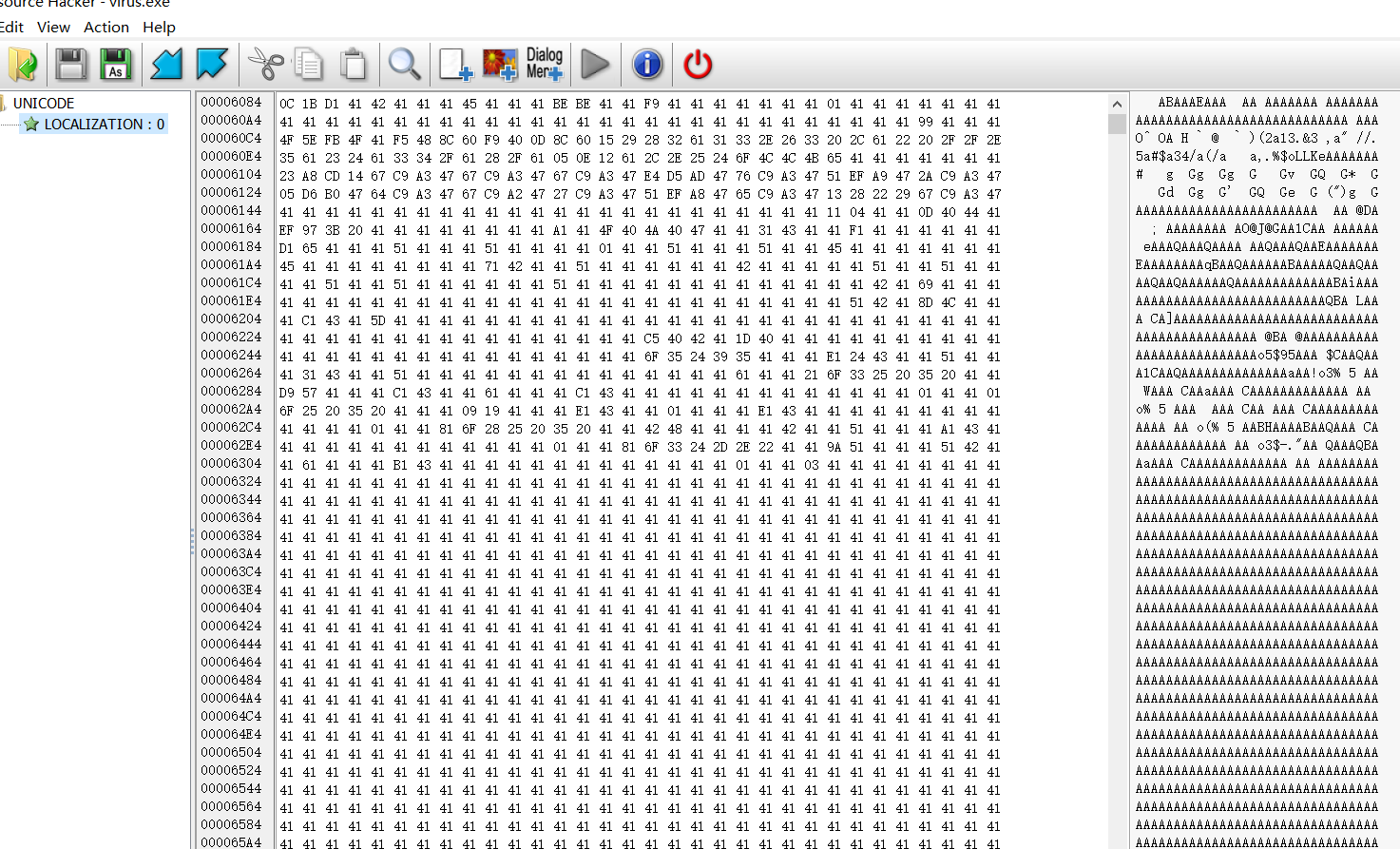 发现好多0x41,我想如果是可执行文件,这些0x41应该是0才对,然后我又异或了开头,发现开头为pe头。那就直接全部异或0x41,保存成新文件继续分析。
发现好多0x41,我想如果是可执行文件,这些0x41应该是0才对,然后我又异或了开头,发现开头为pe头。那就直接全部异或0x41,保存成新文件继续分析。
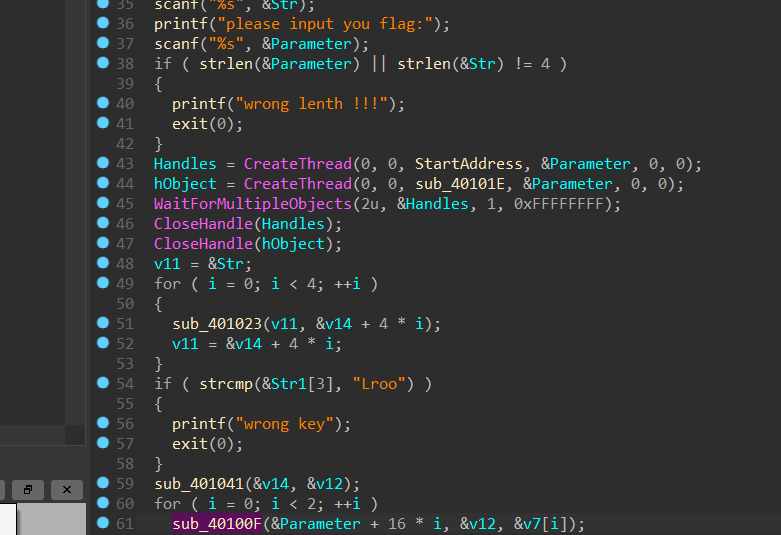
首先会对flag动手脚,然后会对key做手脚,一开始想爆破,爆破了半天,(最后解出来发现首位是特殊字符,寄!)
首先找到key
def key_de(en): |
然后再sub_4012F0中发现是sm4的sbox盒,ck,fk都没改
直接找脚本梭哈
class SM4Cipher: |
Mazeeee
(找屎的题)
32位程序,ida载入
if ( v5 == 22 ) |
打印出地图,三维迷宫路径上只能为O或E,从S出发最终到E,走22步到达,路径规模比较小,直接手过迷宫即可。
S # O # # # # # # O # # # # # |
调试程序下载msvcr100d.dll最新版放在同目录下,下断点到有congratulation处。
for ( i = 0; i < 44; ++i ) |
如下:
from z3 import * |
这样拿到flag后半段是对的,前半段根据hint在strings窗口查看,发现一串base64,直接解码是乱码,对base64表交叉引用发现表经过了变化,即base64换表,写脚本还原即可。
""" |
Crypto
little_trick
签到题,给了p,q,c但是没给e,分别按位加密了dp,dq,只需要挨个还原即可,需要注意的是加密dq那儿是py2,需要用py2跑随机数,还原dp,dq再已知dp,dq,p,q解密。
p=119494148343917708105807117614773529196380452025859574123211538859983094108015678321724495609785332508563534950957367289723559468197440246960403054020452985281797756117166991826626612422135797192886041925043855329391156291955066822268279533978514896151007690729926904044407542983781817530576308669792533266431 |
ez_equation
给了一个方程,我们设三个未知数为a,b,c,那么M1=a*a*b+b*b*a+b*b+a*b
M2=b*b*(c+1)+a*b*(c+1)-2
首先gcd(M1,M2+2)=kb
那么gcd(kb,b)=b
先求出b,然后M1,M2两个方程两个未知数,用z3直接梭出a,c
最后还有两个因子是相邻的,直接扔yafu或者开方取前后两个素数
最后再rsa解密
M1= 3826382835023788442651551584905620963555468828948525089808250303867245240492543151274589993810948153358311949129889992078565218014437985797623260774173862776314394305207460929010448541919151371739763413408901958357439883687812941802749556269540959238015960789123081724913563415951118911225765239358145144847672813272304000303248185912184454183649550881987218183213383170287341491817813853157303415010621029153827654424674781799037821018845093480149146846916972070471616774326658992874624717335369963316741346596692937873980736392272357429717437248731018333011776098084532729315221881922688633390593220647682367272566275381196597702434911557385351389179790132595840157110385379375472525985874178185477024824406364732573663044243615168471526446290952781887679180315888377262181547383953231277148364854782145192348432075591465309521454441382119502677245090726728912738123512316475762664749771002090738886940569852252159994522316 |
Strange
加密的是m|hint,给了m&hint和hint
首先根据hint和m&hint可以知道m中哪些比特为1
然后这些已知为1的比特,设其它未知的比特为x,那么满足copper已知部分明文攻击,求出m|hint,所以最后当m&hint为比特位为1则m对应位为1,当m|hint为1且hint为0则m对应位为1,综上可以还原m所有比特位
n,c,m2,hint=[13002904520196087913175026378157676218772224961198751789793139372975952998874109513709715017379230449514880674554473551508221946249854541352973100832075633211148140972925579736088058214014993082226530875284219933922497736077346225464349174819075866774069797318066487496627589111652333814065053663974480486379799102403118744672956634588445292675676671957278976483815342400168310432107890845293789670795394151784569722676109573685451673961309951157399183944789163591809561790491021872748674809148737825709985578568373545210653290368264452963080533949168735319775945818152681754882108865201849467932032981615400210529003, 8560367979088389639093355670052955344968008917787780010833158290316540154791612927595480968370338549837249823871244436946889198677945456273317343886485741297260557172704718731809632734567349815338988169177983222118718585249696953103962537942023413748690596354436063345873831550109098151014332237310265412976776977183110431262893144552042116871747127301026195142320678244525719655551498368460837394436842924713450715998795899172774573341189660227254331656916960984157772527015479797004423165812493802730996272276613362505737536007284308929288293814697988968407777480072409184261544708820877153825470988634588666018802, 9869907877594701353175281930839281485694004896356038595955883788511764488228640164047958227861871572990960024485992, 9989639419782222444529129951526723618831672627603783728728767345257941311870269471651907118545783408295856954214259681421943807855554571179619485975143945972545328763519931371552573980829950864711586524281634114102102055299443001677757487698347910133933036008103313525651192020921231290560979831996376634906893793239834172305304964022881699764957699708192080739949462316844091240219351646138447816969994625883377800662643645172691649337353080140418336425506119542396319376821324619330083174008060351210307698279022584862990749963452589922185709026197210591472680780996507882639014068600165049839680108974873361895144] |
Web
Ez_TP
存在文件泄露 www.zip
\application\index\controller\Index.php
|
可以通过world注册变量,覆盖$a,$hello。
鉴于题目环境是5.1.37,应该是通过file_get_contents触发phar反序列化。
实测直接phar会报错,限制了数据大小,考虑通过其他格式触发
poc:
|
将序列化内容写入zip注释,需要对特殊字符进行替换
|
生成zip文件
|
读入zip文件并做加密编码
echo urlencode(base64_encode(file_get_contents("2.zip"))); |
请求获取flag:
POST /?s=/index/index/hello&lin=cat+/y0u_f0und_It |
补充:线下战报
安询杯线下决赛取得第二名,获得一等奖。
2021安询杯wp
1.2022第二届网刃杯WP
2.2021NCTF比赛WP
3.2021陇原战疫WP
4.2021bytectf线上WP
5.2021绿城杯wp
6.2021第一届长城杯网络安全大赛WP
7.2021第五空间大赛WP
8.2021网刃杯WP