2021NCTF比赛WP
2021NCTF比赛WP
Misc
SignIn
跳转链接到了https://nctf.h4ck.fun/challenges/NCTF%7BWelcome_to_NCTF_2021!%7D
所以得到flag
NCTF{Welcome_to_NCTF_2021!} |
Hello File Format
提示说1920*1080,然后看一下这个bin文件大小为6220800
发现这个大小正好是1920*1080*3
直接联想到了画图咯
from PIL import Image |

NCTF{TGA_NOT_GTA} |
做题做累了来玩玩游戏吧
notepad++全局搜NCTF
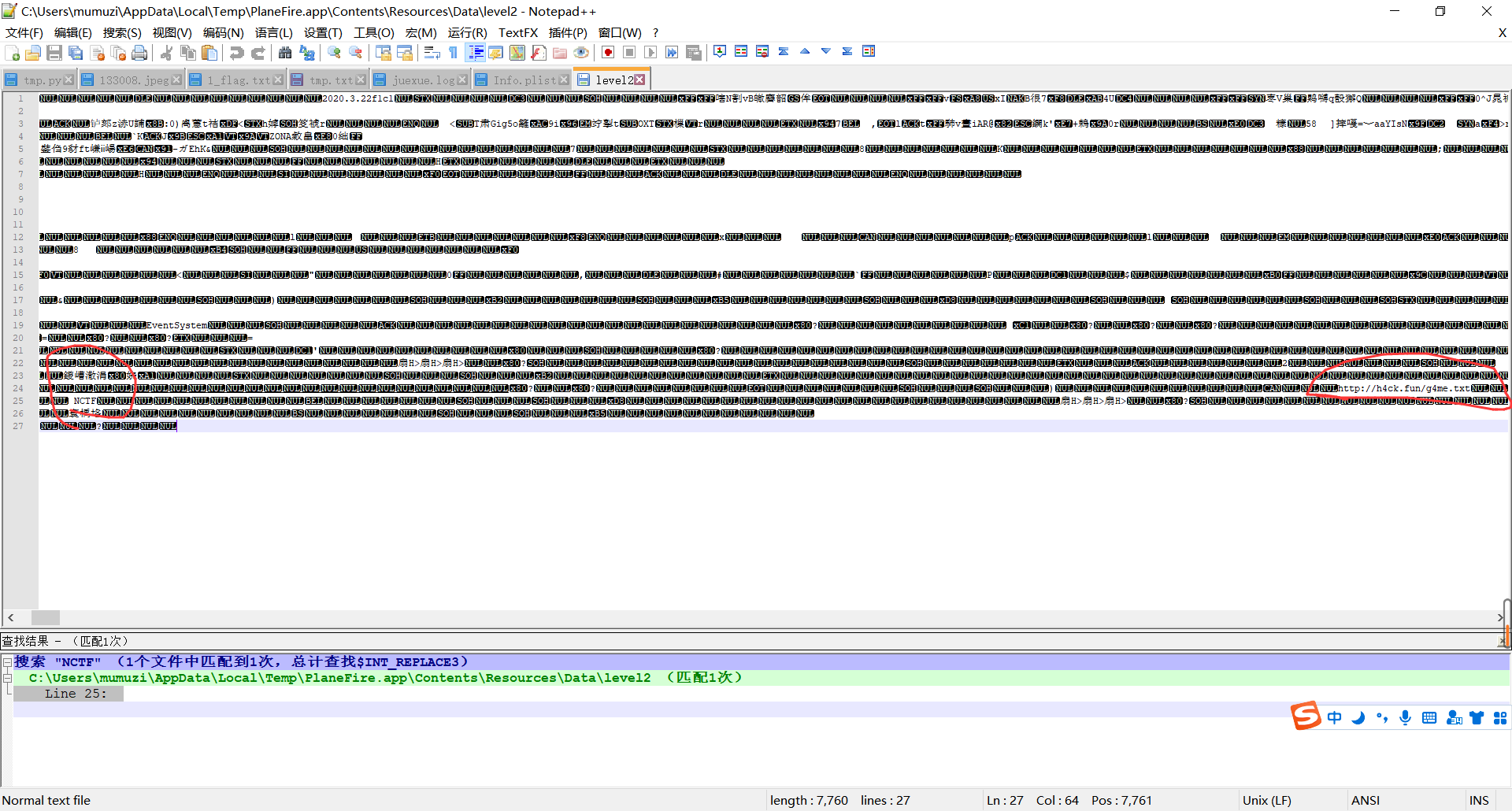
访问那个链接就是flag了
NCTF{B9F3C1F2-1E65-481C-8AF3-A78FA7A5EB6A} |
Pwn
ezheap
思路
有uaf漏洞,直先add+free一波接填满tcache并实现fastbin里出现重复chunk,用泄露函数直接泄露堆地址,然后申请到tcache控制结构体,修改记录tcache里chunk数量的部分,释放tcache控制结构体到unsortedbin,用泄露函数直接泄露libc地址,再打__free_hook就行了。
exp
from pwn import * |
RE
Hello せかい
附件找不到了,总之就是签到题。
Shadowbringer
c++64位程序,ida载入
std::string::string(v4, "U>F2UsQXN`5sXMELT=:7M_2<X]^1ThaWF0=KM?9IUhAsTM5:T==_Ns&<Vhb!", &v6); |
主要用到了c++ string类来进行处理,结合动调,大致经过了两次base64变表加密,在和v4进行比较。
第一组表,
'#$%&',27h,'()*+,-.s0123456789:;<=>?@ABCDEFGHIJKLMNOPQRSTUVWXYZ[h]'+'^_`ab' |
第二组表
'ba`_^]h[ZYXWVUTSRQPONMLKJIHGFEDCBA@?>=<;:9876543210s.-,+*)(',27h,'&''+'%$#' |
两次加密的代码大致相同,主要通过表的长度和每次处理的二进制长度判断为base64.
std::bitset<8ull>::to_string(v13, v14); // 转为2进制 |
了解流程后写解密脚本即可
import base64 |
鲨鲨的秘密
32位程序,ida载入
IpAdress = malloc(0x20u); |
刚载入就有种莫名其妙的熟悉感,和西湖论剑的一道逆向题思路差不多,又是体力活。
是一种修改代码的操作数并单语句执行的SMC,通过一个数组来确定赋值代码长度的大小,和选定相应的操作数和修改的位置。
挖出汇编代码,结合动调分析语句还原算法。
mov ds:dword_403474, 0FFFFFFFFh // mov output ,0xffffffff |
python代码如下
input='a'*40 |
可知是两个字节为一组进行的处理,z3解因为涉及下标问题不好下手,所以直接爆破。
somebox=[0x00000000, 0x77073096, 0xEE0E612C, 0x990951BA, 0x076DC419, 0x706AF48F, 0xE963A535, 0x9E6495A3, 0x0EDB8832, 0x79DCB8A4, 0xE0D5E91E, 0x97D2D988, 0x09B64C2B, 0x7EB17CBD, 0xE7B82D07, 0x90BF1D91, 0x1DB71064, 0x6AB020F2, 0xF3B97148, 0x84BE41DE, 0x1ADAD47D, 0x6DDDE4EB, 0xF4D4B551, 0x83D385C7, 0x136C9856, 0x646BA8C0, 0xFD62F97A, 0x8A65C9EC, 0x14015C4F, 0x63066CD9, 0xFA0F3D63, 0x8D080DF5, 0x3B6E20C8, 0x4C69105E, 0xD56041E4, 0xA2677172, 0x3C03E4D1, 0x4B04D447, 0xD20D85FD, 0xA50AB56B, 0x35B5A8FA, 0x42B2986C, 0xDBBBC9D6, 0xACBCF940, 0x32D86CE3, 0x45DF5C75, 0xDCD60DCF, 0xABD13D59, 0x26D930AC, 0x51DE003A, 0xC8D75180, 0xBFD06116, 0x21B4F4B5, 0x56B3C423, 0xCFBA9599, 0xB8BDA50F, 0x2802B89E, 0x5F058808, 0xC60CD9B2, 0xB10BE924, 0x2F6F7C87, 0x58684C11, 0xC1611DAB, 0xB6662D3D, 0x76DC4190, 0x01DB7106, 0x98D220BC, 0xEFD5102A, 0x71B18589, 0x06B6B51F, 0x9FBFE4A5, 0xE8B8D433, 0x7807C9A2, 0x0F00F934, 0x9609A88E, 0xE10E9818, 0x7F6A0DBB, 0x086D3D2D, 0x91646C97, 0xE6635C01, 0x6B6B51F4, 0x1C6C6162, 0x856530D8, 0xF262004E, 0x6C0695ED, 0x1B01A57B, 0x8208F4C1, 0xF50FC457, 0x65B0D9C6, 0x12B7E950, 0x8BBEB8EA, 0xFCB9887C, 0x62DD1DDF, 0x15DA2D49, 0x8CD37CF3, 0xFBD44C65, 0x4DB26158, 0x3AB551CE, 0xA3BC0074, 0xD4BB30E2, 0x4ADFA541, 0x3DD895D7, 0xA4D1C46D, 0xD3D6F4FB, 0x4369E96A, 0x346ED9FC, 0xAD678846, 0xDA60B8D0, 0x44042D73, 0x33031DE5, 0xAA0A4C5F, 0xDD0D7CC9, 0x5005713C, 0x270241AA, 0xBE0B1010, 0xC90C2086, 0x5768B525, 0x206F85B3, 0xB966D409, 0xCE61E49F, 0x5EDEF90E, 0x29D9C998, 0xB0D09822, 0xC7D7A8B4, 0x59B33D17, 0x2EB40D81, 0xB7BD5C3B, 0xC0BA6CAD, 0xEDB88320, 0x9ABFB3B6, 0x03B6E20C, 0x74B1D29A, 0xEAD54739, 0x9DD277AF, 0x04DB2615, 0x73DC1683, 0xE3630B12, 0x94643B84, 0x0D6D6A3E, 0x7A6A5AA8, 0xE40ECF0B, 0x9309FF9D, 0x0A00AE27, 0x7D079EB1, 0xF00F9344, 0x8708A3D2, 0x1E01F268, 0x6906C2FE, 0xF762575D, 0x806567CB, 0x196C3671, 0x6E6B06E7, 0xFED41B76, 0x89D32BE0, 0x10DA7A5A, 0x67DD4ACC, 0xF9B9DF6F, 0x8EBEEFF9, 0x17B7BE43, 0x60B08ED5, 0xD6D6A3E8, 0xA1D1937E, 0x38D8C2C4, 0x4FDFF252, 0xD1BB67F1, 0xA6BC5767, 0x3FB506DD, 0x48B2364B, 0xD80D2BDA, 0xAF0A1B4C, 0x36034AF6, 0x41047A60, 0xDF60EFC3, 0xA867DF55, 0x316E8EEF, 0x4669BE79, 0xCB61B38C, 0xBC66831A, 0x256FD2A0, 0x5268E236, 0xCC0C7795, 0xBB0B4703, 0x220216B9, 0x5505262F, 0xC5BA3BBE, 0xB2BD0B28, 0x2BB45A92, 0x5CB36A04, 0xC2D7FFA7, 0xB5D0CF31, 0x2CD99E8B, 0x5BDEAE1D, 0x9B64C2B0, 0xEC63F226, 0x756AA39C, 0x026D930A, 0x9C0906A9, 0xEB0E363F, 0x72076785, 0x05005713, 0x95BF4A82, 0xE2B87A14, 0x7BB12BAE, 0x0CB61B38, 0x92D28E9B, 0xE5D5BE0D, 0x7CDCEFB7, 0x0BDBDF21, 0x86D3D2D4, 0xF1D4E242, 0x68DDB3F8, 0x1FDA836E, 0x81BE16CD, 0xF6B9265B, 0x6FB077E1, 0x18B74777, 0x88085AE6, 0xFF0F6A70, 0x66063BCA, 0x11010B5C, 0x8F659EFF, 0xF862AE69, 0x616BFFD3, 0x166CCF45, 0xA00AE278, 0xD70DD2EE, 0x4E048354, 0x3903B3C2, 0xA7672661, 0xD06016F7, 0x4969474D, 0x3E6E77DB, 0xAED16A4A, 0xD9D65ADC, 0x40DF0B66, 0x37D83BF0, 0xA9BCAE53, 0xDEBB9EC5, 0x47B2CF7F, 0x30B5FFE9, 0xBDBDF21C, 0xCABAC28A, 0x53B39330, 0x24B4A3A6, 0xBAD03605, 0xCDD70693, 0x54DE5729, 0x23D967BF, 0xB3667A2E, 0xC4614AB8, 0x5D681B02, 0x2A6F2B94, 0xB40BBE37, 0xC30C8EA1, 0x5A05DF1B, 0x2D02EF8D] |
狗狗的秘密
挺不错的,解完想暴打出题人。
32位程序,ida载入获得假flag一枚
不过main之前有个TlsCallback函数,直接下个断点,动态分析。
if ( !v9 && !IsDebuggerPresent() ) |
反调试,off_825014在主函数出现过,但是个假逻辑,所以这部分内容是SMC修改技术。
unsigned int __cdecl sub_8211F0(unsigned int *a1) |
直接改eip绕过这个反调试即可,同时修改代码用的xTea,不过delta的值有个小坑,main函数中有个创建线程的函数,将delta赋值为0xDA76C600,patch进行修改,后面下个断F9。
修复函数后拿到真正处理逻辑。
int __cdecl sub_823000(const char *a1) |
delta的值是0,需要注意一下,接着就是写脚本逆向,z3不好直接求解,加密流程是先将输入转为47进制下每位的值存在数组v11中,找到第一个非0值的下标k,接着进行单表替换和异或。
因为涉及到表索引和本身异或不好逆向还原,所以想着在爆破v11数组。
enc=[0x52, 0xC3, 0x1A, 0xE0, 0x16, 0x5D, 0x5E, 0xE2, 0x67, 0x1F, 0x1F, 0x06, 0x06, 0x1F, 0x17, 0x06, 0x0F, 0xF9, 0x06, 0x67, 0x58, 0xB2, 0xE2, 0x8C, 0x0F, 0x2A, 0x06, 0x89, 0xCF, 0x2A, 0x06, 0x1F, 0x98, 0x1A, 0x3E, 0x17, 0x67, 0x1F, 0xF7, 0x3A, 0x44, 0xC3, 0x16, 0x33, 0x69, 0x1A, 0x75, 0x16, 0x3E, 0x17, 0xD5, 0x69, 0x7A, 0x1B, 0x44, 0x44, 0x3E, 0x67, 0xF7, 0x89, 0x67, 0xC3] |
v11第一位是0,根据加密的最后一位是0xc3,或者多次测试都可知,不过这解有点多,下面就是对c进行排列组合,之后47进制转,long_to_bytes下即可,不过这…..tmd,dfs不太会写,直接硬爆破了,大概跑了半小时,直接整emo了。
完整如下
from Crypto.Util.number import * |
*easy_mobile
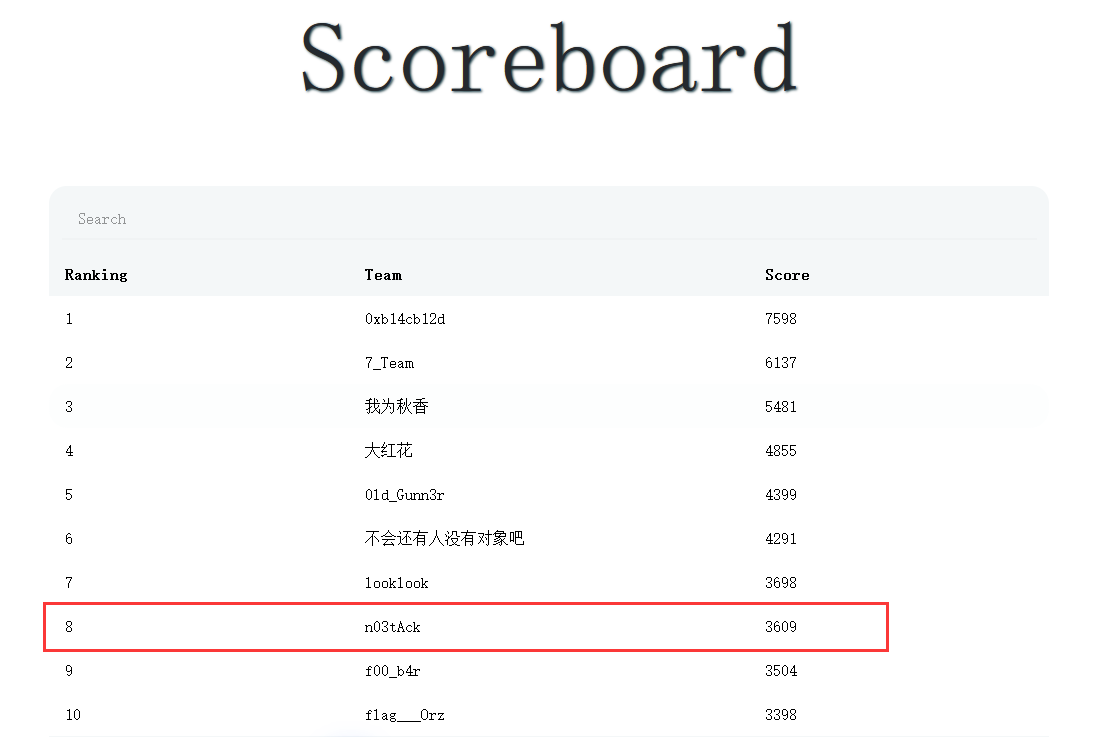
为了保7-10名拿衣服纪念品所以控分没交
so被ollvm了,1400行。
但是我用deflat去混淆,最后只剩三分一的代码?,没法只能用原来的看。
我尝试去动调,发现下不了断点?
想到只有1400行而已。
然后我比较菜,花了一个多小时才整理了逻辑。
首先,我在719行找到了获取输入
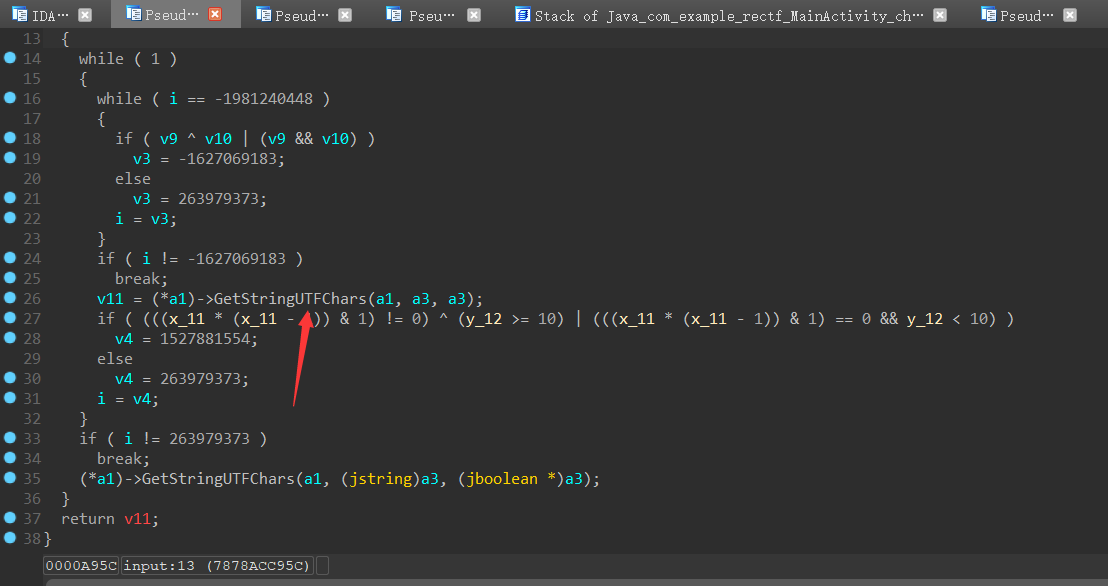
然后发现判断长度为24
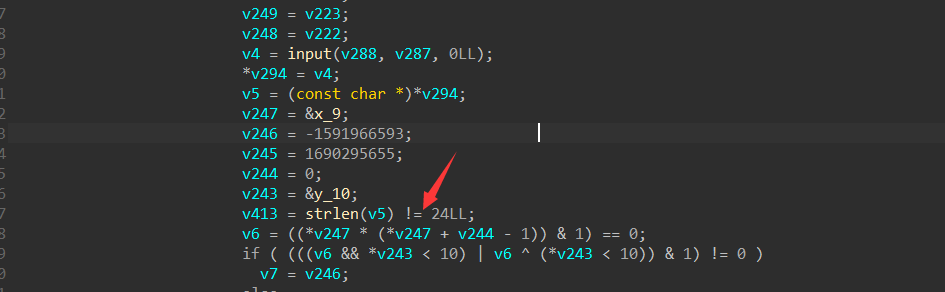
交叉索引我们的输入
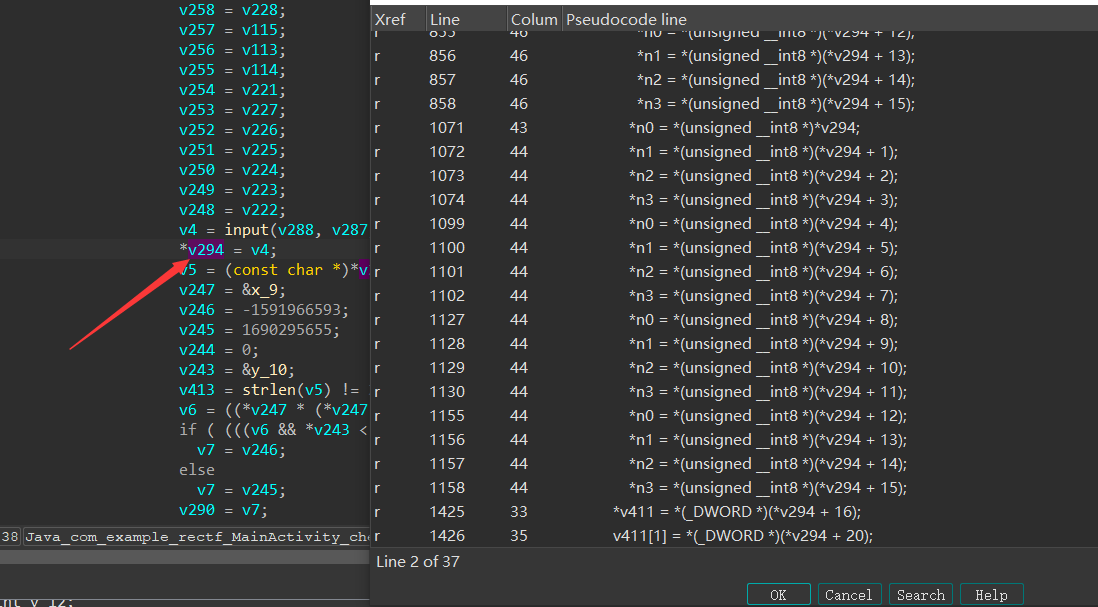 发现,程序会将前16个字节分成4个字节一组分成四组的进行操作,最后8个字节分成两组。
发现,程序会将前16个字节分成4个字节一组分成四组的进行操作,最后8个字节分成两组。
我先看了程序对后面八个字节进行了什么操作
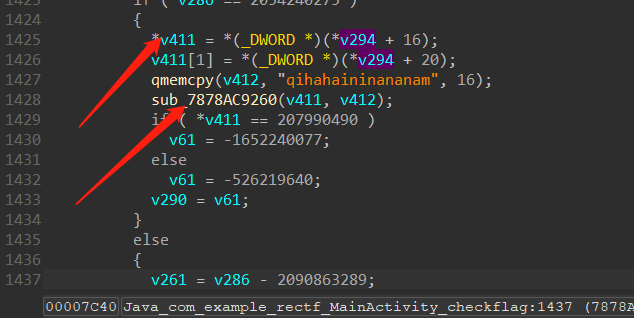
他作为输入传进了下面这个函数。并且上面还将一个长为16字节的字符串传了进去
跟进去看了一下
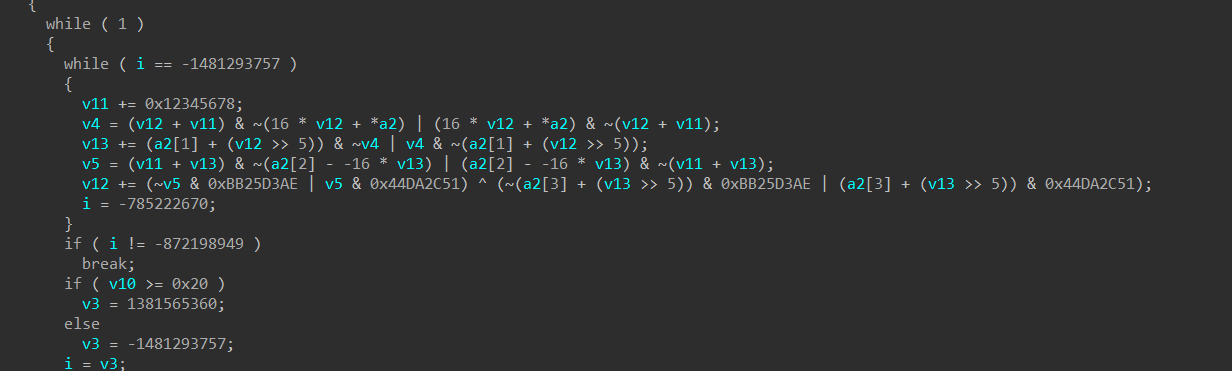
我顿时反应过来了,这和tea怎么那么像?
然后我手动恢复了一下
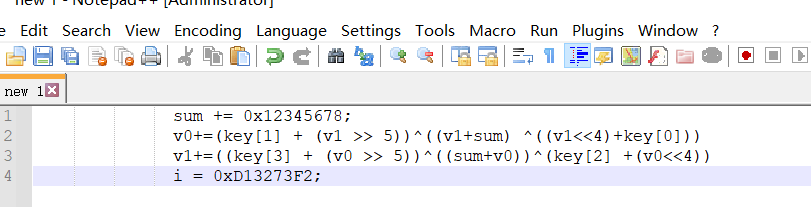
这不就是改了delta但还是原汁原味的tea吗?而且他a2就是我们传入的第二个字符串,那就是KEY
我直接用我祖传脚本梭哈得到了我们后8个字符。
|
然后去继续交叉索引到第一次被调用的地方
然后理解一下

就是将我们的前4个字符,保存在一个int32x4的数据类型中,可以理解为他是一个大小为四的int32类型数组。
下面一样的操作,当取完前16个字节后,他会取一些常量,如下

然后整理一下就是这也
v48 = *v299; // [0x20,0x22,0x23,0x24] |
一开始尝试爆破,然后我发现我傻了,直接求逆不就行了?然后一把梭
enc=[ 0x00000CD7, 0x00000698, 0x00000D7C, 0x000006FA, 0x00000CB7, 0x000007CA, 0x0000079B, 0x000007D2, |
e0a0d966076ff43758af2715
Crypto
signin
对h/k连分数展开可以求到p
def transform(x,y): |
2021NCTF比赛WP
1.2022第二届网刃杯WP
2.2021安询杯wp
3.2021陇原战疫WP
4.2021bytectf线上WP
5.2021绿城杯wp
6.2021第一届长城杯网络安全大赛WP
7.2021第五空间大赛WP
8.2021网刃杯WP